SQL Injection in WordPress Websites
SQL (Structured Query Language) is a way of communicating with databases to power web applications. Moreover, databases store and display information of users through these apps.
Unquestionably, WordPress SQL injection vulnerability is ranked as the second most critical security vulnerability. Whereas, attackers can control data in a database by sending designed demands through an input parameter.
What is an SQL Injection Attack?
SQL injection(SQLi), attacks a web application where malicious SQL statements can gain access and manipulate the underlying database. Besides, it is comparable to a Cross-site scripting (XSS) attack. Whereas introducing JavaScript code, it utilizes SQL instructions. To illustrate, if the attack is successful, the following situations can occur:
- Stealing credentials: SQL injections can be employed to acquire users’ credentials. However, attackers can gain their authorizations and then masquerade as these users.
- Gaining database access: Attackers can utilize SQL injections to access data stored in a database server.
- Manipulating data: Attackers can employ SQL injections to alter or eradicate the reached database.
- Accessing networks: Attackers can exploit SQL injections to enter database servers with operating system privileges.
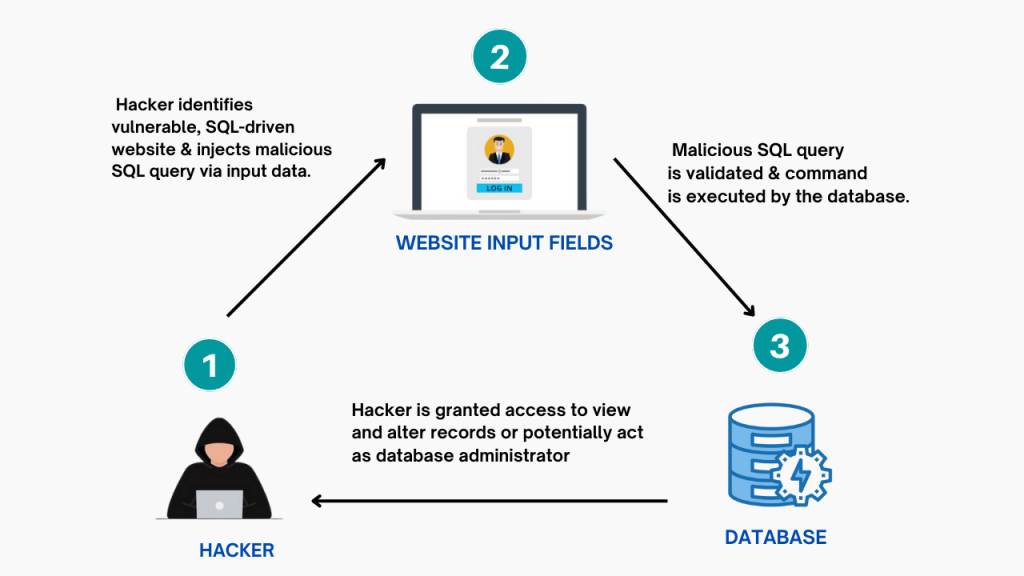
Examples of an SQL Attack
An attacker can use malicious code can gain access to an app server’s database by manipulating a website form. While hackers can input a SQL statement in the URL query string or POST data (like HTML forms) which executes against the database.
For instance, if a form asks for your name and address but does not filter the input. Thus, an attacker could enter something like INSERT INTO the user’s VALUES (‘DROP TABLE users;). As well as, deleting all user data from the database.
How to Prevent Injection?
1. Input validation
The validation process serves to verify that the data provided by a user is valid. However, validation checks if it is the desired type, length, format, etc. This helps to prevent any unauthorized commands from being accepted. Undoubtedly, it is like looking through the peephole before opening the door.
Using regular expressions for structured data (such as name, age, earnings, survey response, and postcode) to ensure adequate input authentication. Despite a list of predetermined values (like dropdown menus or radio buttons), make certain which one is returned. By this, the incoming data must match one of the offered selections precisely. The below shows how to carry out table name validation.
switch ($tableName) {
case ‘UMPTable’: return true;
case ‘MetaTable’: return true;
default: return new ErrorMessageException(‘unexpected value provided as table name’);
}
The $tableName variable can then be directly appended. Undoubtedly, it is now widely known to be one of the legal and expected values for a table name.
2. Parametrized queries
Parameterized queries are a way of pre-constructing an SQL statement. Unlike this, you can feed the parameters for it to be carried out. This technique enables the database to identify the code and differentiate it from the data input. The user input is automatically protected and the provided information will not alter the purpose, thereby helping prevent an SQL injection attack.
PDO (PHP Data Objects) uses techniques that make using parameterized queries easier. Also, it renders the code more legible and transferable, as it works with many different databases aside from MySQL. The below code uses PDO with parameterized queries to prevent SQL injection vulnerability.
<?php
$id = $_GET[‘id’];
$db_connection = new PDO(‘mysql:host=localhost;dbname=ump_test, ‘dbuser’, ‘dbpasswd’);
//preparing the query
$sql = “SELECT username
FROM users
WHERE id = :id”;
$query = $db_connection->prepare($sql);
$query->umpPRO(‘:id’, $id);
$query->execute();
//getting the result
$query->setFetchMode(PDO::FETCH_ASSOC);
$result = $query->fetchColumn();
print(htmlentities($result));
3. Avoid Dynamic SQL
Dynamic SQL has the potential to introduce insecurity into the system, as it creates an automated way of generating and enacting commands. To dodge a SQL injection attack, it is sensible to employ prepared statements, parameterized questioning, or stored procedures for your WordPress page.
4. Adopt the latest technologies
Previous web development tools lack SQLi defense. However, utilize the updated variant of the advancement environment and language, as well as the most recent technologies associated with that platform/speech. For example, in PHP apply PDO instead of MySQLi.
5. Use a Web Application Firewall
The most efficient way to safeguard your WordPress website is to install a firewall. Moreover, this security system inspects and regulates all data that enters your site, and forms another layer of protection from SQL injection attacks. Also, our WordPress security solutions feature a firewall. It automates the Secure Sockets Layer (SSL) setup and utilization of the Cloudflare Content Delivery Network (CDN).
6. Remove Unnecessary Database Functionality
The more features a database has, the more open it is to a potential SQL injection attack. Also, helps to protect it, think about organizing your database by eliminating unnecessary data and making your site less at risk.
7. Encrypt Confidential Data
No matter how safe your database may feel, there are always methods to ensure it is more secure. Thus, by encrypting sensitive data within your databases, you can provide protection from any potential SQL injection.
8. Avoiding administrative privileges
It is not advisable to link your program to the database via an account with root privileges, except if it is completely necessary. Besides, this could be dangerous as intruders may gain control of the entire system. Even so, accounts with limited power on the server can compromise the safety of your application more. In addition, when multiple databases and applications are hosted on that server.




